Stay Safe Bug
During the Covid pandemic, every country has its own app or service to help track and monitor citizens for infection. And to prevent spread.
One of these was the Stay Safe app. Before being bought by the Philippine government, this was developed by a company called MultiSys. I have checked their website and that’s it. One thing I know is that their email doesn’t work.
The Bug
I don’t have a Stay Safe account but one thing I know is that they were using a third-party called Uploadcare for handling the assets. What are these assets? These are the photos of every person in the Philippines who signed up and their government-issued IDS. And some other personal stuff like a selfie I guess. I know there’s a selfie because of a class named ConfirmSelfieActivity.java.
Based on my analysis, this bug only exists in v2.* and was fixed in v3.*. Or removed.
The issue was rather simple and preventable. The developers hardcoded both private and public keys in the code to be used in the UploadCare API. You can see in the photo below, the variables UPLOAD_CARE_PRIVATE_KEY and UPLOAD_CARE_PUBLIC_KEY.
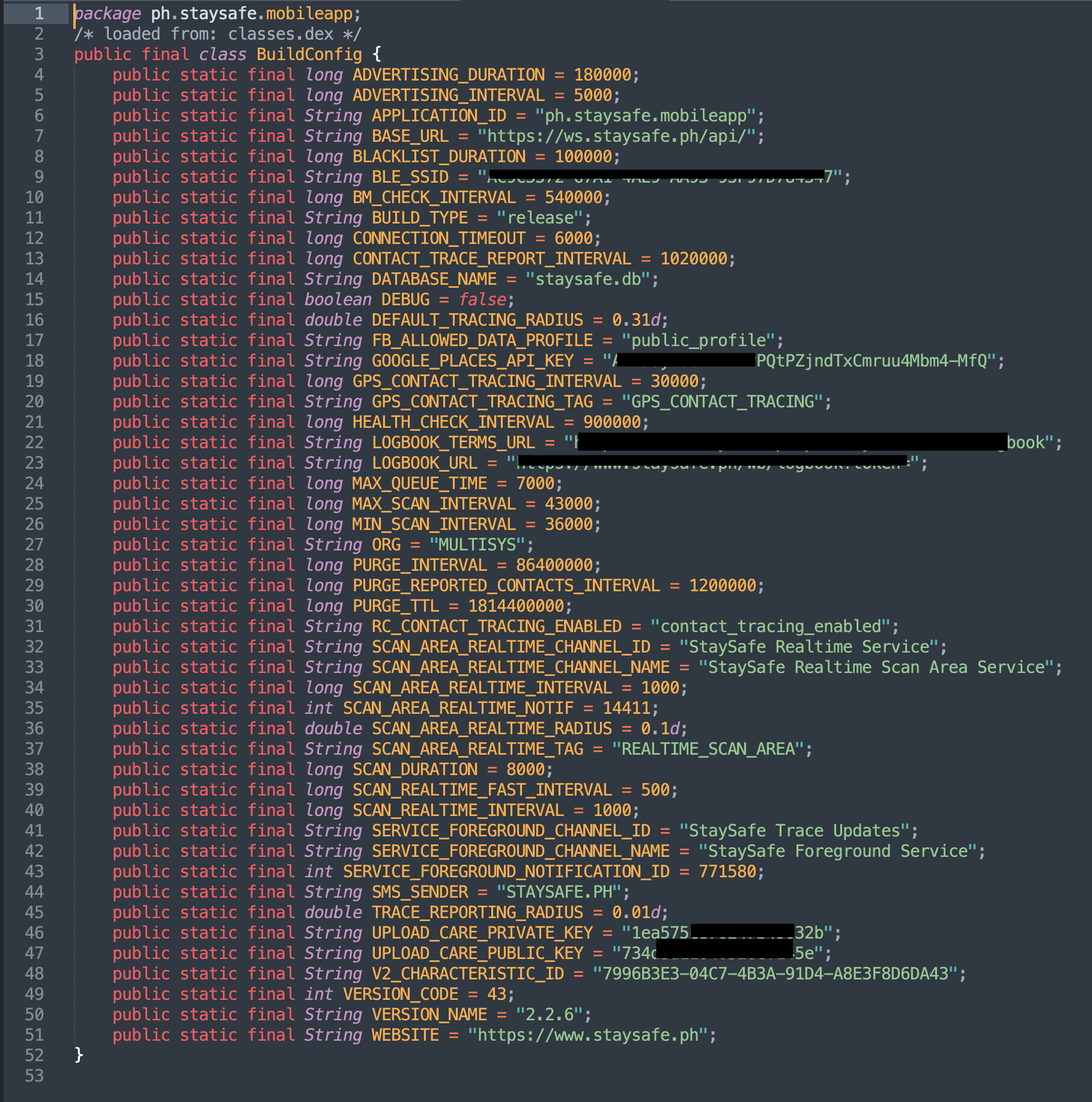
You only need these two keys to communicate with the UploadCare API. So anyone, who knows how to decompile an Android app, can retrieve all the data uploaded by every user.
By just calling the API URL https://api.uploadcare.com with the HTTP Header Uploadcare.Simple <UPLOAD_CARE_PUBLIC_KEY>:<UPLOAD_CARE_PRIVATE_KEY> you can communicate and retrieve all the data.
The code block below is confirmation that all you need are the two sets of keys.
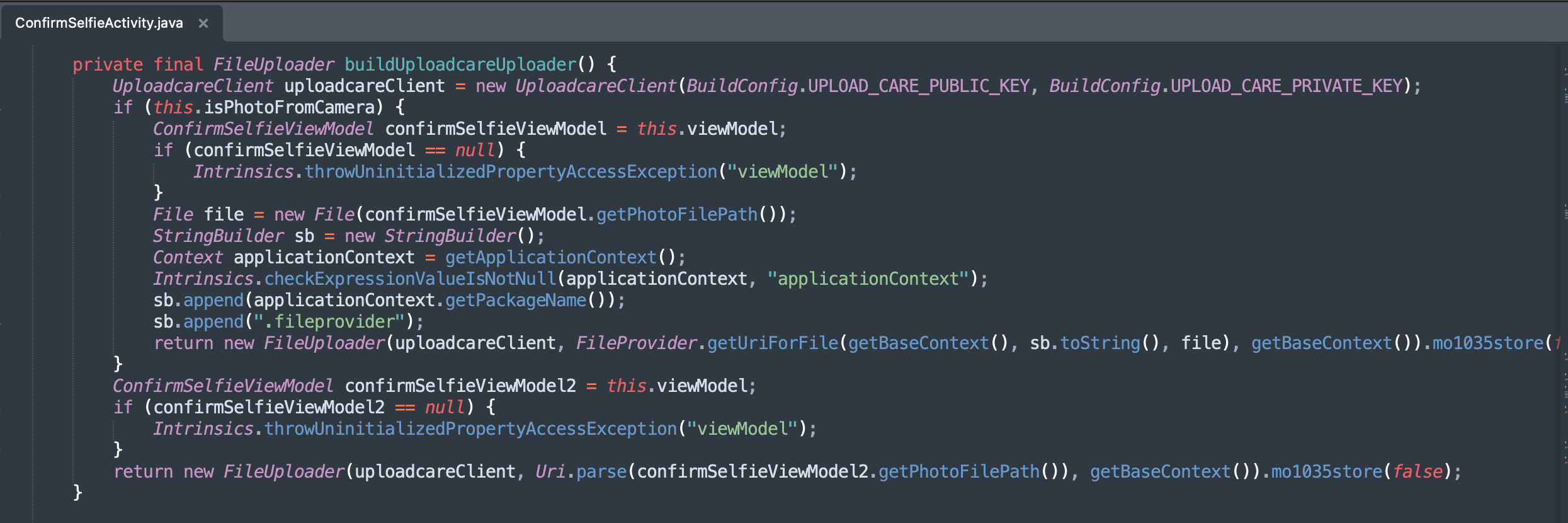
This was very reckless for the developers and company. The app wasn’t obfuscated too. Let this be a lesson to not hardcode your keys in the code.